
Hacked WordPress Sites Suck!
Back in November my company J Computer Solutions LLC was the subject of a WordPress hack that affected all of my client and personal websites! This was an expensive lesson in security and eventually I recovered my client data! As a result of this experience I have decided to share with you what I did to help those who are also experiencing the same thing. I’m even going to throw in some tips to prevent this from happening in the first place!
How It All Started
So one day I get a bunch of emails from my monitoring app that is telling me that not one, not two but ALL OF MY WORDPRESS sites were down. No sooner I start getting a barage of calls and texts from my clients complaining that their websites (many of whom, these sites were the backbone of their businesses) where down. After talking to each client individually I narrowed down the cause. One of my clients had installed a cracked plugin to avoid paying the original developer. I promptly removed him from my service.
What Was The Hack
The hack would place <script> tags on every .php page and in every post in the database that would cause a series of redirects to a bunch of spam sites. This happened on all of my WordPress sites and the first thing I noticed was that all of the sites were going redirecting to the same series of three URLs. Knowing that the hack was caused by a plugin and not a human meant that if I could reverse engineer the hack, I could come up with a algorithmic solution to fix all of my hacked WordPress sites.
Fix: wp export & RegEx
I knew I wasn’t going to go through all the .php files and remove the malware; way too many files and the database is more important I can always reinstall WordPress. That being said I decided the best thing to do was the following
- Install a fresh version of the website on a new server
- Export the post, page and product data using the wp cli
- Use RegEx to find and replace malware data with appropriate data
Luckily I use Laravel Forge and can manage my WordPress installations from a dashboard. I created a fresh database and fresh WordPress instance.
On the old instance, I SSH’d into the machine and ran the following command in the website directory
wp export
This will generate a .xml file that contains all of the post, page and product data. After opening the .xml file in Atom I see one of the URLs immediately
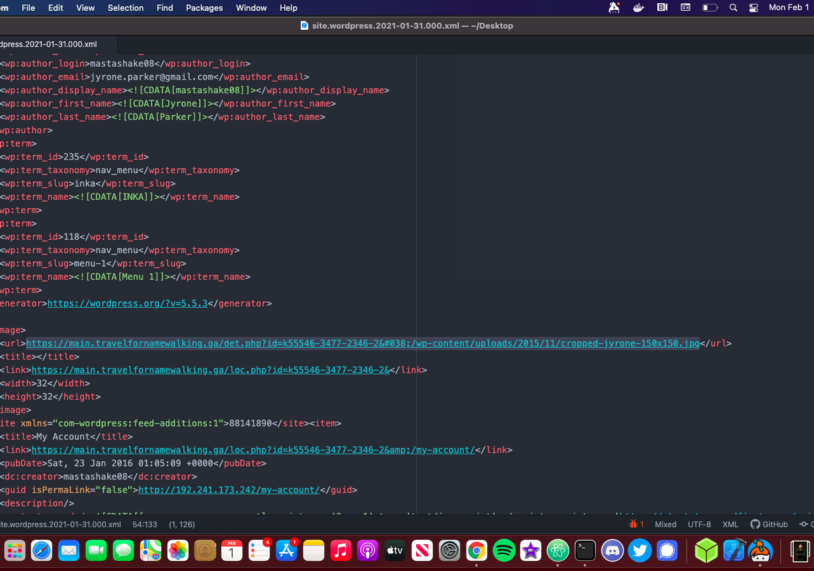
Atom has some great RegEx find and replace functionality I needed to replace all these URLs with the URL of the website here is an example for this site.
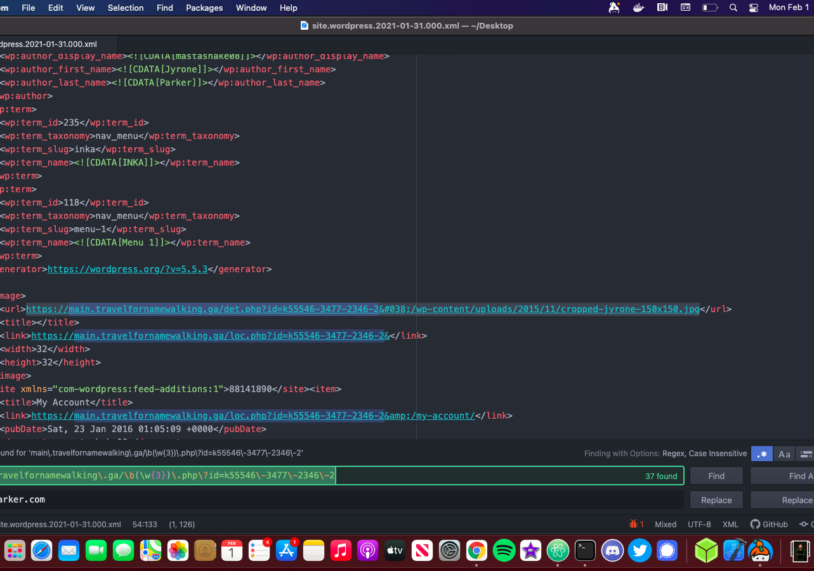
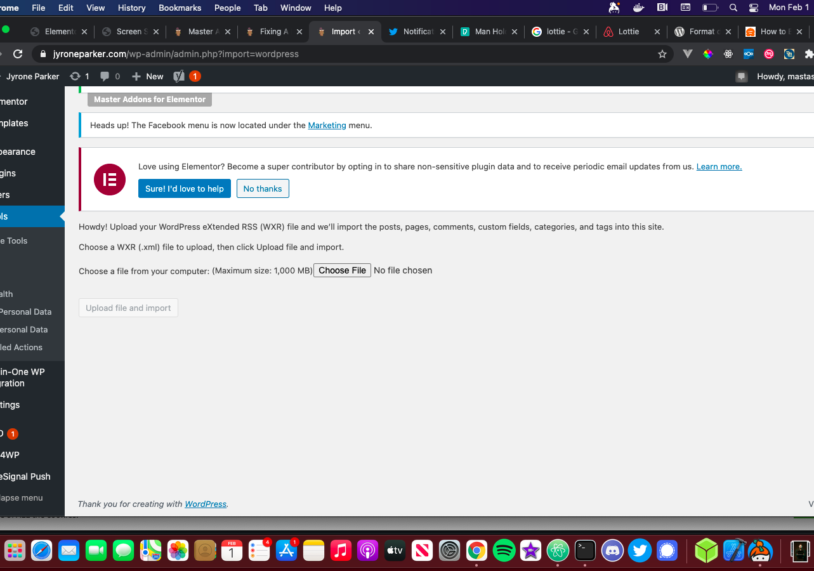
After replacing all malware URLs you can save the .xml file and head back to your fresh installation. Head over to tools -> import and select the default WordPress importer. Simply upload the XML file and you should have your site back hack free!
Hacks Are Horrible
However they can be mitigated, I hope this tutorial helps anyone who experienced the same hack I did and can get their sites back up. If this did help you please share the blog post!
